In this issue, we sorted out several items that were hot in March, including network, backend, database, visualization tools, etc.
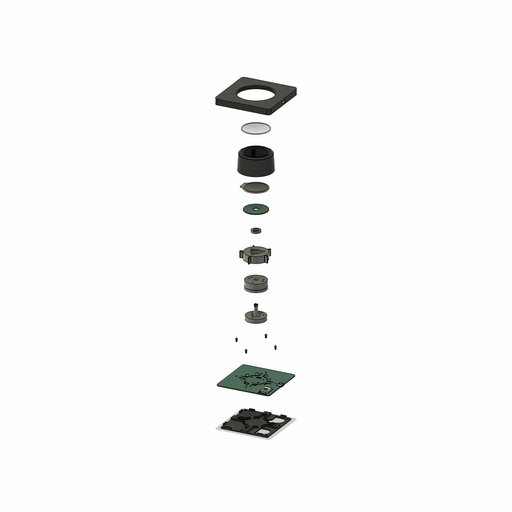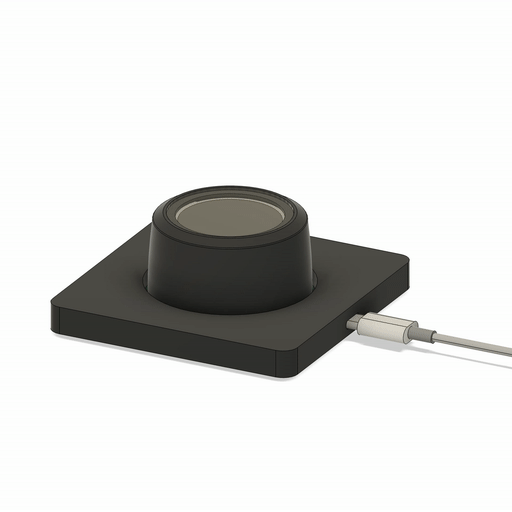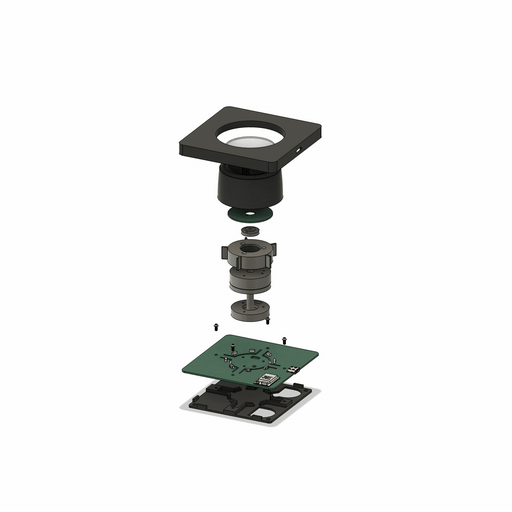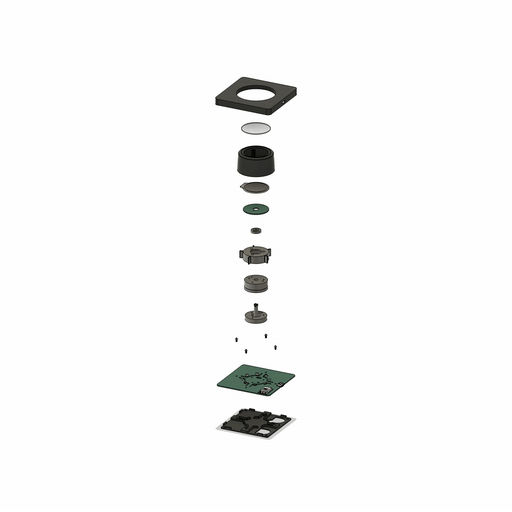
SmartKnob
SmartKnob is an open source input device with a software-configurable brake and virtual locator. A brushless gimp motor is paired with a magnetic encoder to provide closed-loop torque feedback control so that the feel of the ratchet and limiter can be dynamically created and adjusted. Although this is a “DIY” open source project, it is not yet a full-fledged plug and play project. If you intend to build it yourself, note that it requires advanced welding experience to build – surface mount soldering with very small spacing is required (reflow or hot air is recommended), and assembly is time-consuming and delicate.
Open source: Apache
Project address:
https://github.com/scottbez1/smartknob
OpenBB terminal
OpenBB Terminal provides a modern integrated Python-based environment for investment research, enabling the average retail trader to leverage state of the art data science and machine learning techniques. As a modern Python-based environment, OpenBBTerminal is open to data science (Pandas, Numpy, Scipy, Jupyter), machine learning (Pytorch, Tensorflow, Sklearn, Flair) and data acquisition (Beautiful Soup, etc.) Access to Python databases. Third-party apis).
Open source License: MIT License
Project address:
https://github.com/OpenBB-finance/OpenBBTerminal

hackingtool
hackingtool as an all-in-one tool set for hackers, can help us better understand some network attack and defense related knowledge. The tool set mainly includes anonymous hiding tools, information collection tools, word generator, wireless attack tools, SQL injection tools, phishing attack tools, network attack tools, late exploitation tools, forensics tools, payload creation tools, reverse engineering tools using framework, DDOS attack tools, remote administrator tools, (RAT)XSS Attack tools, steganography tools, etc.
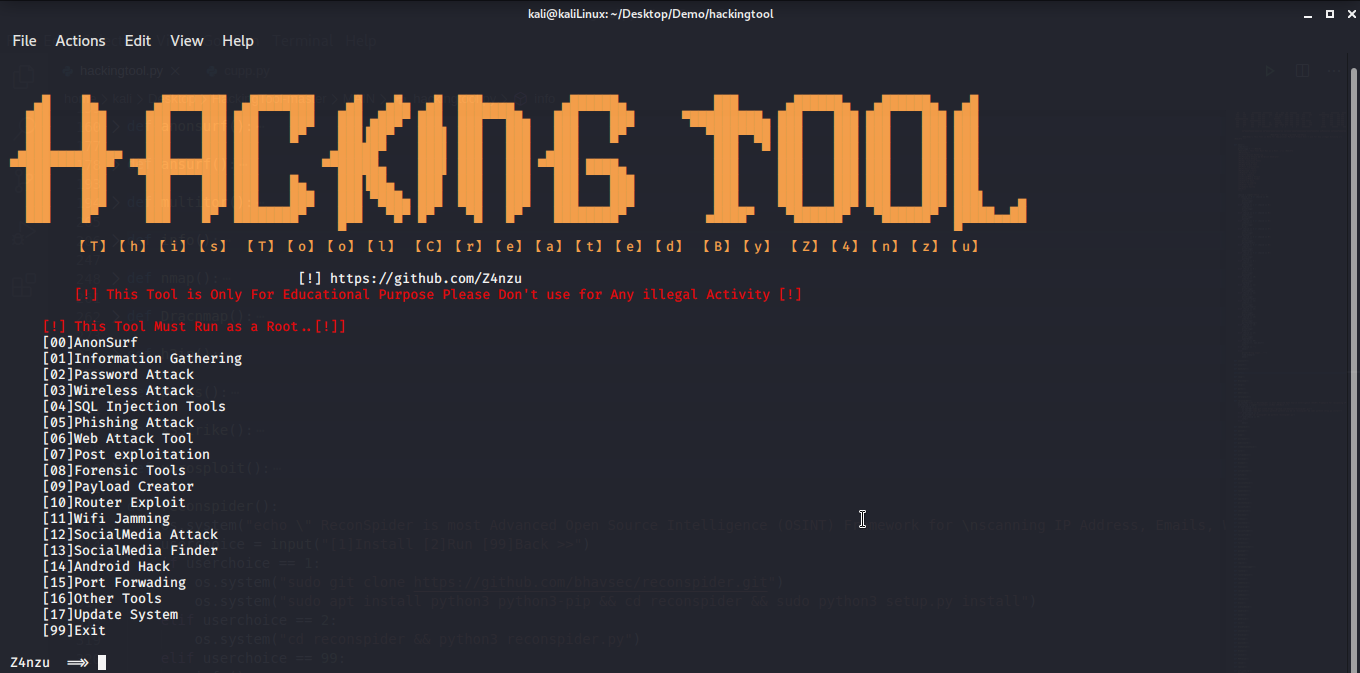
Open source License: MIT License
Project address:
https://github.com/Z4nzu/hackingtool
Terminal editor Helix
Helix is first a terminal-based editor that lets you explore a custom renderer (similar to emacs) in wgpu or skulpin, The tools include VIM-like modal editing, multiple selection, built-in language server support, intelligence via tree-sitter, incremental syntax highlighting, and code editing.
Open source: MPL-2.0 License
Project address:
https://github.com/helix-editor/helix
Grafana Mimir
Grafana claims to be the most scalable and high-performance open source temporal database in the world. Mimir supports scaling metrics to a billion or more, with simplified deployment, high availability, multi-tenancy, persistent storage, and ultra-fast query performance up to 40 times faster than Cortex. Mimir also includes some commercial features, such as infinite cardinality using horizontally scalable, “split” compressors, and fast, high-cardinality queries via sharded query engines.

Open source: AGPL-3.0 License
Project address:
https://github.com/grafana/mimir
Mastodon open source social network server
Mastodon is a free and open source social networking server based on ActivityPub, where users can follow their friends and discover new friends. On Mastodon, users can post anything they want: links, images, text, videos. All Mastodon servers can interoperate as a federated network (users on one server can communicate seamlessly with users on another server, including the non-Mastodon software that implements ActivityPub).
Open source: AGPL-3.0 License
Project address:
https://github.com/mastodon/mastodon
Kestra’s infinitely scalable orchestration and scheduling platform
Kestra is an infinitely scalable orchestration and scheduling platform that can create, run, schedule, and monitor millions of complex pipelines. Workflows can start simple and grow to more complex systems with branching, parallelism, dynamic tasks, process dependencies, and Kestra also has a built-in Web interface that allows you to create, run, and monitor all of your processes – no need to deploy your processes, just edit them.

Open source: Apache-2.0 License
Project address:
https://github.com/kestra-io/kestra
Peergos Private networks that end users can control
The foundation of
Peergos is a peer-to-peer encrypted global file system with fine-grained access controls designed to prevent monitoring of data content or friendship graphs. It will have a secure messenger, optional interoperability with email, and a fully private and secure social network where users can control who sees what (executed encrypted).

Open source: AGPL-3.0 License
Project address:
https://github.com/Peergos/Peergos
litestreamSQLite independent stream replication tool
Litestream is a stand-alone stream replication tool for SQLite. It runs as a background process and securely copies changes incrementally to another file or S3. Litestream only communicates with SQLite through the SQLite API, so it won’t damage your database.

Open source: Apache-2.0 License
Project address:
https://github.com/benbjohnson/litestream
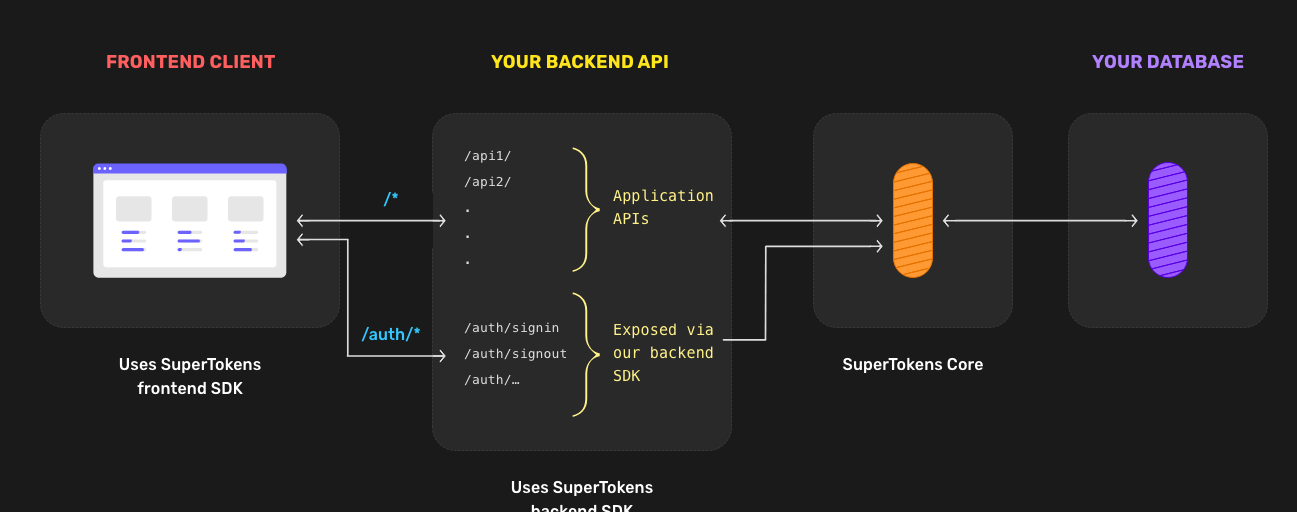
Open source authentication provider
Add secure login and session management to your application. SDKS available for popular languages and front-end frameworks, such as Node.js, Go, Python, React.js, React Native, Vanilla JS, and others.
- Local deployment so that you control 100% of the user data using your own database.
- End-to-end solution with login, registration, user, and session management without all the complexities of the OAuth protocol.
- Easy implementation and higher security.
Open source: Apache-2.0 License
Project address:
https://github.com/supertokens/supertokens-core
Hook framework LSPosed
The Riru/Zygisk module attempts to provide an ART hook framework that utilizes the LSPlant hook framework to provide an API consistent with OG Xposed. You can have multiple modules that can make changes to the same part of the system or application. For the modified APK, you must choose one. There is no way to combine them, unless the author has built multiple APKs with different combinations.
Open source: GPL-3.0 License
Project address:
https://github.com/LSPosed/LSPosed
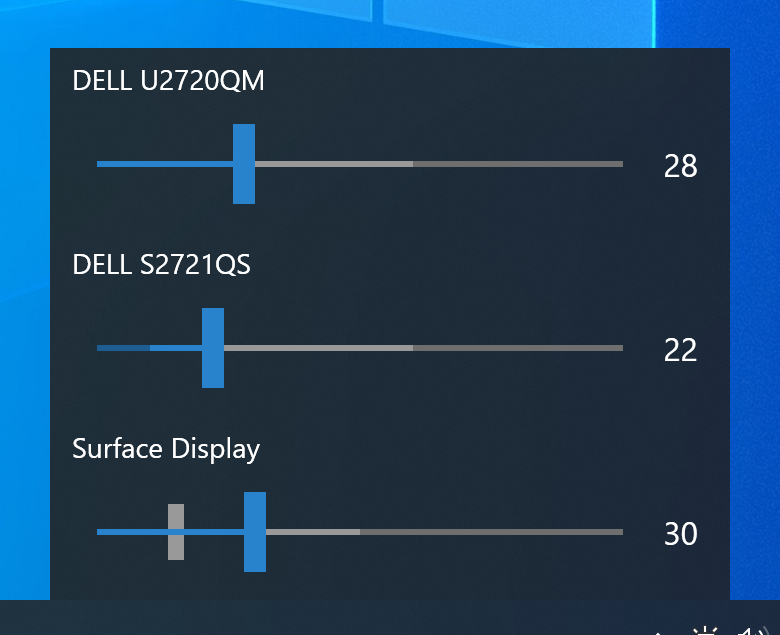
Monitorian Windows desktop tool to easily adjust the brightness of multiple monitors
The user can change the brightness of the display individually or uniformly, including the brightness of the external display. For systems with ambient light sensors, the adjusted brightness can be displayed along with the configured brightness. In addition, users can seamlessly change the adjustable range of brightness and contrast of each display, the operation interface supports Chinese, and the display needs to turn on DDC/CI when using.
Open source license: View license
Project address:
https://github.com/emoacht/Monitorian
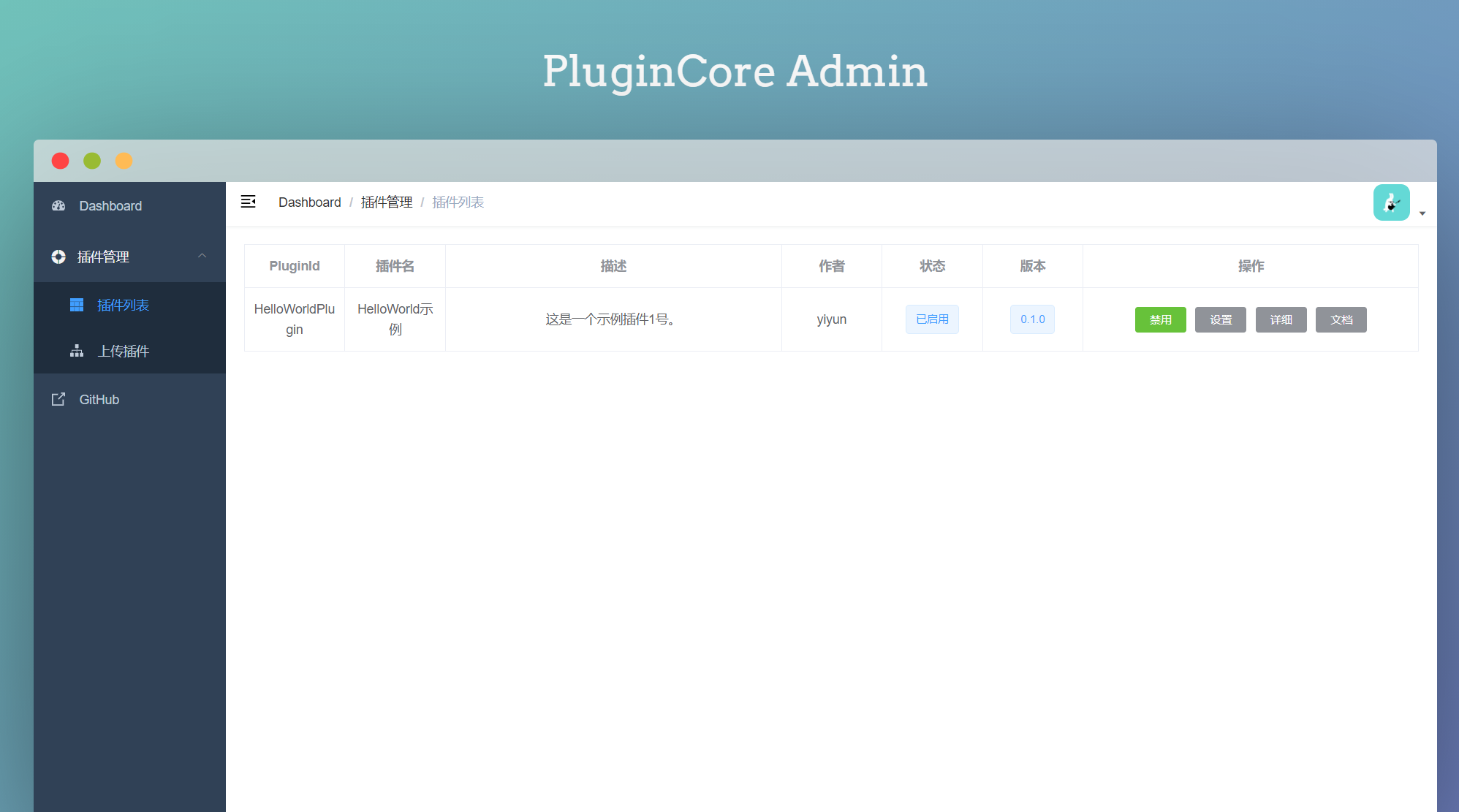
Lightweight plugin framework for ASP.NET Core
PluginCore mainly includes front-end automatic integration, two lines of code to complete the integration, each plug-in can add Controller, has its own route, You can apply for DI in the constructor method of the plug-in class that implements IPlugin, and of course, you can also apply DI in the Controller constructor method. You can embed extension points in the front end, and then insert widgets and other functions through the plug-in, which is very powerful.
Open source: Apache-2.0 License
Project address:
https://github.com/yiyungent/PluginCore
Free Windows screenshot recording tool
ShareX supports full-screen screenshots, rolling screenshots, detection window screenshots, GIF recording, etc. After screenshots, it also supports adding text, watermark, special effects, Mosaic, etc. Finally, it can directly upload pictures to get links, and complete the whole screenshot process smoothly.
Open source: GPL-3.0 License
Project address:
https://github.com/ShareX/ShareX
Gogs a self-service Git service that is easy to build
The
Gogs (/gɑgz/) project aims to build a simple, stable, and extensible self-service Git service in the easiest way possible. Development in Go enables Gogs to be distributed as a stand-alone binary and supports all platforms supported by Go, including Linux, macOS, Windows, and ARM platforms.

Open source License: MIT License